TPRM Technology Stack for Healthcare: Tools, Platforms, and Integration Strategies
Post Summary
Healthcare organizations face growing risks from third-party vendors, which account for 35% of cyberattacks in the sector. With over 276 million health records breached in 2024 alone, ensuring Protected Health Information (PHI) security and regulatory compliance is urgent. Traditional methods like spreadsheets can't keep up, making Third-Party Risk Management (TPRM) technology essential.
Key takeaways:
- Centralized vendor inventory: Tracks vendor details and risk levels.
- Automated risk assessments: Saves time and ensures real-time monitoring.
- Identity and Access Management (IAM): Restricts vendor access to sensitive data.
- Censinet RiskOps™: A healthcare-specific platform simplifying TPRM with automation and AI.
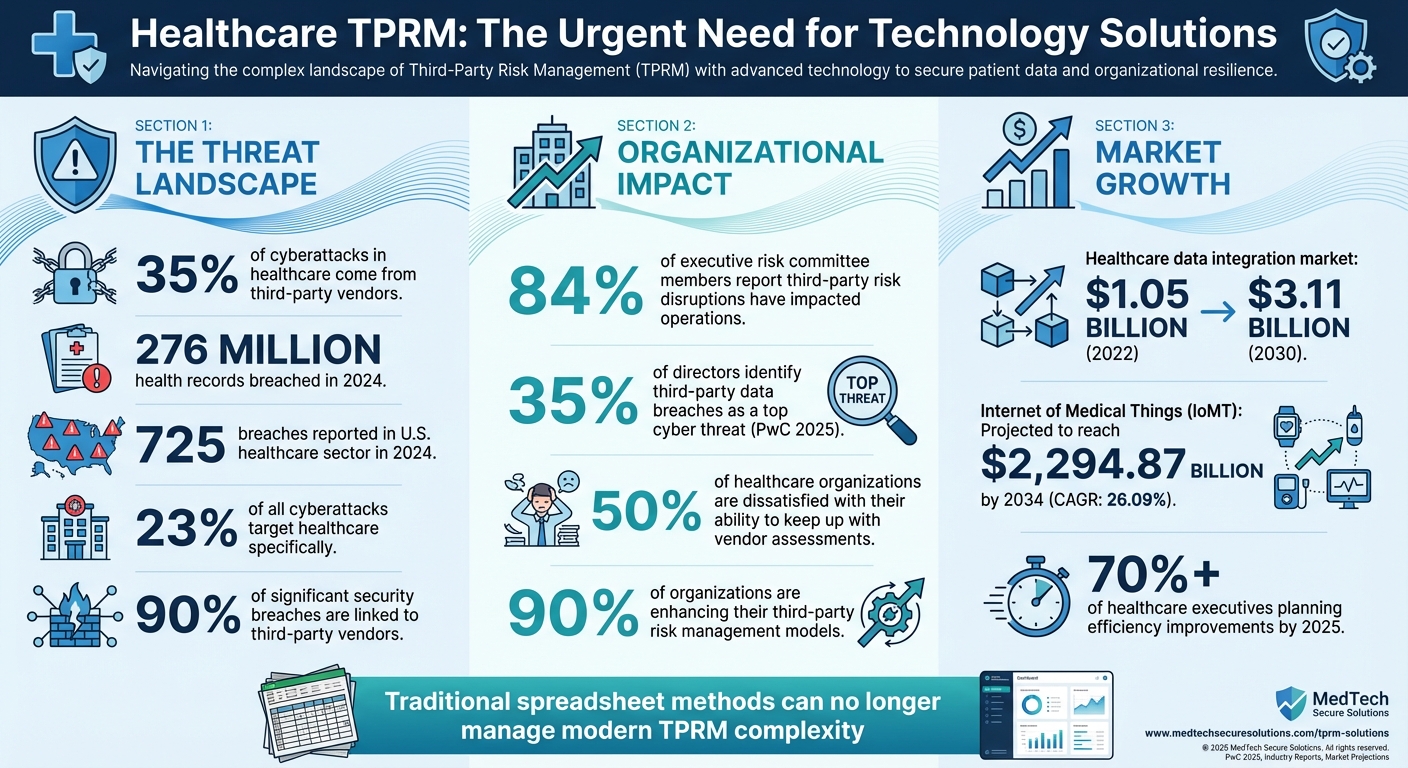
Healthcare Third-Party Risk Management Statistics and Impact
Core Components of a Healthcare TPRM Technology Stack
Creating an effective TPRM (Third-Party Risk Management) technology stack is all about achieving visibility, automation, and secure vendor management. These elements help healthcare organizations move away from outdated, scattered spreadsheets to a streamlined system that tracks risks in real time. Each component plays a critical role in managing third-party relationships and mitigating risks.
Centralized Vendor Inventory and Risk Classification
A centralized vendor database acts as the go-to resource for managing all third-party relationships. This system keeps track of essential vendor details, such as contract terms, security certifications, and the type of data they handle. Without this centralized view, it’s almost impossible for organizations to reliably monitor vendor counts, oversee responsibilities, or track access to sensitive data like Protected Health Information (PHI).
Risk classification takes this a step further by organizing vendors into tiers based on two main factors: how much sensitive data they access and how critical their services are to the organization [1]. For example, high-risk vendors - like EHR (Electronic Health Record) providers or cloud storage services managing PHI - demand more frequent assessments and stricter oversight. On the other hand, lower-risk vendors, such as office supply providers with no access to sensitive data, require minimal monitoring. This tiered system ensures that resources are focused where they’re needed most, avoiding wasted effort on low-impact vendors while maintaining strict oversight of high-risk ones. Centralization and classification together support proactive risk management and compliance, both of which are essential for healthcare organizations.
Automated Risk Assessment and Monitoring Tools
Manual risk assessments can be a major drain on time and resources, often leading to inefficiencies. In fact, 50% of healthcare organizations report dissatisfaction with their ability to keep up with the sheer volume of vendor assessments [5]. Automation changes the game by simplifying repetitive tasks like sending questionnaires, collecting evidence, tracking remediation efforts, and generating compliance reports [4].
These tools also provide continuous monitoring instead of relying on one-time assessments. For instance, if a vendor experiences a security breach or misses a certification renewal, automated systems can flag the issue immediately. This kind of real-time visibility is crucial, especially when 90% of significant security breaches are linked to third-party vendors [5]. Automated risk scoring further enhances efficiency by helping security teams prioritize their efforts, focusing on the most urgent vulnerabilities first.
Identity and Access Management (IAM) Integration
Controlling who has access to what data is a cornerstone of secure third-party interactions. IAM solutions integrate seamlessly with TPRM platforms to enforce key security measures like Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Just-in-Time (JIT) access controls. These tools ensure vendors only have access to the systems and data they need for their specific tasks, significantly reducing potential risks.
Integration capabilities, such as API connections, are equally important. They allow risk data to flow securely between the TPRM platform and other enterprise systems, including EHRs and security tools [4]. This interconnected ecosystem eliminates data silos and keeps access permissions updated across all systems. For example, if a vendor’s risk classification changes or their contract ends, IAM integration can automatically adjust their access rights. This not only saves time but also minimizes the chances of human error, which can lead to security vulnerabilities.
Censinet RiskOps™: The Central Platform for Healthcare TPRM
Censinet RiskOps™ is a comprehensive platform designed to tackle the unique challenges of third-party and enterprise risk management in healthcare. Unlike generic tools, it’s specifically built to address critical issues like protecting patient health information (PHI), managing risks tied to clinical applications, medical devices, and navigating the complexities of healthcare supply chains. At its core, Censinet RiskOps™ demonstrates how modern technology can integrate advanced automation to safeguard healthcare delivery, offering features tailored to the specific needs of healthcare organizations.
Features and Capabilities of Censinet RiskOps™
Censinet RiskOps™ combines risk assessments, cybersecurity benchmarking, and collaborative risk management into a single, streamlined system. Its benchmarking tools provide healthcare organizations with critical context for making informed risk decisions. Within its shared network, healthcare delivery organizations (HDOs) and their vendors can collaborate seamlessly, breaking down communication silos and ensuring all stakeholders access real-time data.
The platform’s command center offers an intuitive dashboard for risk visualization, enabling security teams to quickly assess their overall risk landscape. From identifying high-priority vendor vulnerabilities to addressing compliance gaps, the dashboard provides instant insights that empower teams to act swiftly and effectively.
Censinet AITM and AI for Faster Risk Management
Censinet AITM simplifies the traditionally time-consuming process of vendor assessments. It allows vendors to complete security questionnaires instantly, summarizes vendor evidence and documentation, and generates detailed risk summary reports based on assessment data. This eliminates common bottlenecks and accelerates the assessment process.
Building on this, Censinet AI introduces a layer of automation guided by human oversight. It handles critical tasks like evidence validation, policy creation, and risk mitigation. With configurable rules and review processes, the system keeps risk teams in control while enabling healthcare organizations to scale operations without compromising safety. Acting like "air traffic control" for Governance, Risk, and Compliance (GRC) processes, the AI routes and prioritizes tasks, ensuring that critical findings are directed to the right stakeholders at the right time. These capabilities translate into tangible benefits, allowing healthcare organizations to operate more efficiently while maintaining a strong focus on patient safety.
Benefits of Using Censinet for Healthcare Organizations
By leveraging Censinet RiskOps™, healthcare organizations can manage cyber risks more effectively while maintaining accuracy and safety. The platform’s automation and AI capabilities reduce the workload associated with large volumes of vendor assessments, enabling security teams to concentrate on high-risk vendors and emerging threats.
Censinet also strengthens compliance efforts by centralizing documentation, automating reports, and providing real-time tracking of vendor certifications and remediation activities. This centralized approach is especially beneficial during audits or regulatory reviews, where easily accessible evidence simplifies the compliance process. Most importantly, these improvements directly protect patient safety by reducing the risk of data breaches, system outages, or disruptions in care delivery.
Integration Strategies for TPRM Technology
Integrating Censinet RiskOps™ with your existing systems ensures a smoother transition while avoiding disruptions and preventing the creation of data silos. Starting with a well-planned approach lays the groundwork for effective workflow mapping and seamless data integration.
Mapping Workflows and Prioritizing Integrations
Begin by cataloging your existing PHI systems and vendor relationships. Focus on systems that involve frequent vendor interactions, such as procurement platforms and GRC tools, for integration with Censinet RiskOps™. This centralized approach not only streamlines vendor risk management but also highlights legacy systems that may need to be replaced.
Using API Connectivity for Data Migration
Leveraging API integration creates a unified, authoritative source for vendor data, eliminating inconsistencies across departments. When Censinet RiskOps™ connects to systems like ERP, procure-to-pay, and accounts payable, vendor data flows seamlessly. This ensures consistent risk ratings and real-time certification updates without the need for manual input. The result? Enhanced processes and more comprehensive risk management.
Phased Rollout and Change Management
Adopt a phased approach to rolling out Censinet RiskOps™. Start with a pilot program in a single department to fine-tune processes before expanding across the organization. Gain executive support by showcasing visual dashboards that emphasize the urgency of TPRM and its potential impact. Schedule training sessions for all departments to ensure a smooth adoption process and clearly communicate cybersecurity requirements and vendor risks to staff.
"Cybersecurity strategies for healthcare encompass proactive approaches to risk assessment, third-party oversight, and regulatory compliance using tools like AI and automation" [3].
This phased and well-structured rollout not only simplifies integration but also sets the stage for scalable, forward-thinking TPRM solutions.
sbb-itb-535baee
Building and Scaling a Future-Ready TPRM Technology Stack
TPRM Implementation Maturity Model
Healthcare organizations typically follow a step-by-step path when developing their Third-Party Risk Management (TPRM) capabilities. The journey starts with the basics: creating a vendor inventory and classifying risks. This involves documenting all third-party relationships and sorting them by risk level. From there, organizations move to standardized assessments, which streamline questionnaires and establish consistent evaluation methods across departments. As the process evolves, automation and continuous monitoring take center stage. Tools like Censinet RiskOps™ simplify routine tasks and provide real-time insights into risks. At the most advanced stage, predictive risk management powered by AI steps in, helping organizations anticipate and address potential threats before they materialize.
With over 70% of healthcare executives planning to focus on efficiency improvements by 2025, advancing through these stages isn’t just a goal - it’s a necessity [2]. However, as organizations mature their TPRM processes, they must also allocate budgets wisely and tailor their strategies to support these advanced capabilities.
Cost Considerations and Custom Plans
Effective TPRM requires thoughtful budgeting. Costs typically include software licensing, hardware upgrades, API development, testing, training, and ongoing IT support [2]. The growing emphasis on interoperability is reflected in the global healthcare data integration market, which reached $1.05 billion in 2022 and is projected to climb to $3.11 billion by 2030 [2].
To meet the diverse needs of healthcare organizations, Censinet offers three flexible service models:
- Platform-Only: Ideal for organizations with the internal expertise to manage the software independently.
- Hybrid Mix: Combines platform access with managed services for specific tasks, offering a balanced approach.
- Fully Managed Services: Designed for organizations that prefer to outsource their entire cyber risk management process.
This flexibility ensures that even smaller healthcare providers, often working with limited resources, can implement robust TPRM solutions that rival those of larger enterprises.
Maintaining Long-Term Success and Compliance
Building a TPRM system is just the first step - maintaining and improving it over time is equally important. With cybersecurity threats constantly evolving, organizations must adopt scalable practices and aim for continuous improvement. For instance, the 725 breaches reported in the U.S. healthcare sector in 2024 highlight the ongoing risks [2], while 23% of all cyberattacks target healthcare specifically [3].
Regular reviews are critical. Quarterly audits of assessment completion rates, remediation timelines, and vendor compliance can help organizations stay ahead of potential risks. Additionally, updating risk assessment criteria to align with new regulations and standards is essential. The rapid growth of the Internet of Medical Things (IoMT) - projected to reach $2,294.87 billion by 2034, with a CAGR of 26.09% - means that TPRM systems must be equipped to handle an ever-increasing number of connected devices [2].
Tools like Censinet RiskOps™ play a crucial role by automatically integrating industry best practices and regulatory updates. This ensures that your risk management strategy remains effective and relevant. Together, these efforts create a strong foundation for a resilient and future-ready TPRM technology stack in the healthcare sector.
Conclusion and Key Takeaways
Healthcare organizations are under increasing pressure to manage the complexities of third-party vendor relationships. With 84% of executive risk committee members noting that third-party risk disruptions have impacted their operations [6] and 35% of directors identifying third-party data breaches as a top cyber threat in PwC's 2025 Global Digital Trust Insights survey [8], the urgency for a strong third-party risk management (TPRM) system is clear. These challenges highlight the importance of adopting a streamlined, automated TPRM solution.
An effective TPRM platform offers tangible benefits: stronger security, reduced costs, enhanced visibility into data, quicker vendor onboarding, and more efficient audits [9]. These improvements not only lower operational risks but also ensure compliance with critical regulations like HIPAA and other healthcare-specific requirements.
The move toward centralized risk management is gaining momentum, with 90% of organizations enhancing their third-party risk management models [7]. This shift reflects the reality that manual processes can no longer meet the demands of modern vendor management. Tools like Censinet RiskOps™ simplify the process by combining centralized vendor tracking, automated assessments, and AI-powered analysis, all while maintaining essential human oversight.
Building a future-ready TPRM system requires thoughtful planning, seamless integrations, and ongoing refinement. Whether your organization opts for a platform-only approach, a hybrid model, or fully managed solutions, selecting tools that align with your specific needs, budget, and long-term goals is crucial. As Diligent aptly puts it, "For companies in regulated sectors, managing risk in third-party relationships is non-negotiable and a growing focus for boards and stakeholders" [8].
FAQs
How does Censinet RiskOps™ improve third-party risk management for healthcare organizations?
Censinet RiskOps™ transforms third-party risk management in healthcare by automating assessments, delivering real-time insights, and organizing critical data within an easy-to-navigate dashboard. These tools empower healthcare organizations to quickly spot and tackle risks while staying compliant with the industry's strict regulations.
By incorporating features like continuous monitoring, AI-driven analytics, and simplified workflows, Censinet RiskOps™ minimizes manual work, enhances decision-making, and safeguards sensitive patient information. Plus, its smooth integration with current IT systems makes vendor management more efficient throughout every stage of the process.
What are the main advantages of integrating Identity and Access Management (IAM) with TPRM platforms?
Integrating Identity and Access Management (IAM) with Third-Party Risk Management (TPRM) platforms offers healthcare organizations a range of important advantages. For starters, it strengthens security by ensuring that only authorized individuals can access sensitive vendor data, effectively lowering the chances of breaches or unauthorized access.
Beyond security, this integration streamlines user management by centralizing access controls, which simplifies compliance with regulatory standards. It also plays a critical role in addressing insider threats by restricting access to essential systems. Plus, with real-time monitoring of user activity across vendor networks, organizations gain improved oversight and accountability, making it easier to track and manage interactions.
Why is automation essential for managing third-party risks in healthcare?
Automation has become a game-changer in managing third-party risks within the healthcare industry. It simplifies intricate processes and boosts efficiency by enabling real-time risk detection and automating repetitive tasks such as vendor assessments and compliance questionnaires. By reducing the likelihood of human error, automation ensures organizations can keep a constant eye on their vendors and tackle risks before they escalate.
Incorporating automation into third-party risk management allows healthcare organizations to bolster cybersecurity, streamline compliance processes, and safeguard sensitive patient information. At the same time, it helps save valuable time and resources. This dual benefit not only enhances day-to-day operations but also strengthens the entire supply chain against potential threats.
Related Blog Posts
- Common Healthcare Third-Party Risk Assessment Questions
- Third-Party Risk Management vs. Vendor Management: What Healthcare Leaders Need to Know
- Healthcare Third-Party Risk Management Trends 2025: What's Changing and Why It Matters
- Healthcare Third-Party Risk Management Maturity Model: Where Does Your Organization Stand?


