Guide to Encryption for International Healthcare Compliance
Post Summary
Encryption is now a must for securing healthcare data across borders. Here's why: regulations like GDPR, HIPAA, and others demand strong encryption to protect sensitive patient information during storage and transfer. With global privacy laws tightening - especially after rulings like Schrems II - organizations face stricter requirements for cross-border data protection.
Key takeaways:
- TLS 1.2/1.3 is the standard for encrypting data in transit.
- AES-256 is widely used for securing data at rest.
- HIPAA 2026 updates make encryption mandatory, removing its "addressable" status.
- GDPR compliance often requires supplementary encryption measures for data transfers outside the EU.
- Emerging methods like homomorphic encryption allow secure data analysis without decryption.
Organizations must also manage encryption keys securely, conduct Transfer Risk Assessments (TRA), and align with frameworks like Standard Contractual Clauses (SCCs) for international transfers. Tools like Censinet RiskOps™ can simplify compliance by automating risk assessments and vendor management.
Encryption isn't just about meeting legal requirements - it's about safeguarding patient trust in an increasingly interconnected world.
How Healthcare Organizations Can Protect Patient Data with Azure HIPAA Compliance
sbb-itb-535baee
International Compliance Standards and Their Encryption Requirements
International Healthcare Encryption Standards Comparison: HIPAA, GDPR, HITECH, PIPEDA, and APPI Requirements
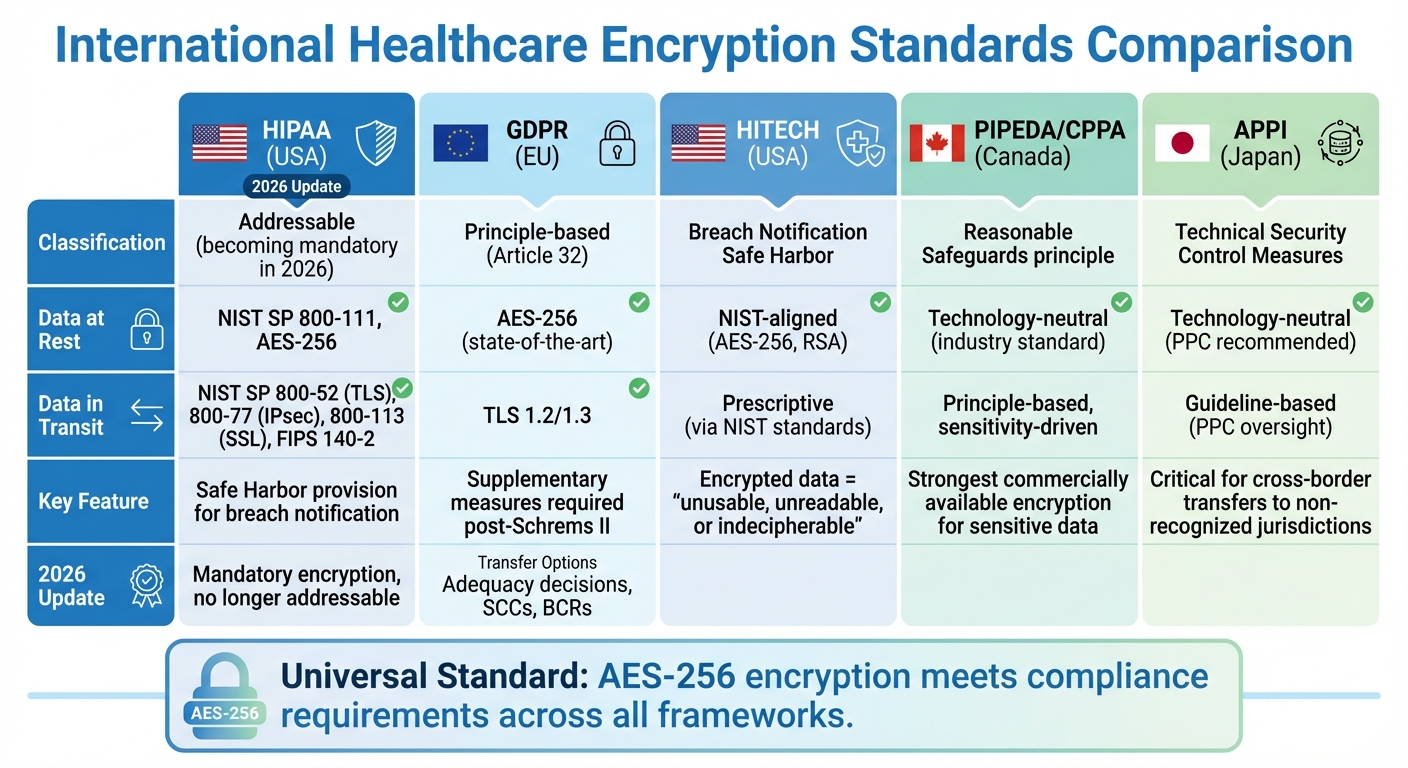
Healthcare organizations working across multiple countries must carefully navigate encryption rules specific to each region. While the introduction gave a broad overview of international compliance, understanding the technical details of key regulations is critical for successful implementation. Frameworks like HIPAA, GDPR, and regional standards such as PIPEDA and APPI each have their own take on encryption, ranging from detailed technical guidelines to more flexible, principle-based approaches. Here’s a closer look at how these regulations address encryption for both data at rest and data in transit.
HIPAA Encryption Requirements and 2026 Updates
HIPAA describes encryption as "an algorithmic process that scrambles data to render it unusable without a confidential key" [2]. While encryption is classified as "addressable", organizations must provide documented alternatives if they choose not to implement it [3].
Technical standards under HIPAA are clear:
- Data at rest must comply with NIST Special Publication 800-111, Guide to Storage Encryption Technologies for End User Devices.
- Data in motion must adhere to NIST SP 800-52 (TLS), 800-77 (IPsec VPNs), 800-113 (SSL VPNs), or FIPS 140-2 validation [2].
The Office for Civil Rights emphasizes the importance of keeping decryption tools separate from the data they encrypt:
To avoid a breach of the confidential process or key, these decryption tools should be stored on a device or at a location separate from the data they are used to encrypt or decrypt.
In 2026, HIPAA introduced updates to address the growing threat of cyberattacks. Following a Notice of Proposed Rulemaking in early 2025, the Department of Health and Human Services rolled out changes that include mandatory multi-factor authentication and stricter vulnerability management. These updates, shaped by nearly 5,000 public comments, reflect a growing focus on robust technical safeguards [4].
Organizations that encrypt ePHI following NIST standards can achieve "safe harbor" status under the HIPAA Breach Notification Rule. This means that if encrypted data is lost or stolen but the encryption key remains secure, it may not qualify as a reportable breach [2].
GDPR Encryption Requirements for EU Healthcare Data
Unlike HIPAA, GDPR adopts a less rigid but equally demanding approach. Article 32 highlights encryption as a key method for securing data both at rest and in transit, though it doesn’t prescribe specific technical standards [5][6]. Typically, organizations use TLS 1.2/1.3 for data in transit and AES-256 for data at rest to meet the "state-of-the-art" requirement [7].
For data transfers outside the European Economic Area, GDPR Chapter V requires that protections remain consistent with EU standards [5]. The European Data Protection Board explains:
The GDPR aims to guarantee an equivalent level of protection to personal data being transferred to the one they enjoy within the EEA.
There are three main options for lawful data transfers:
- Adequacy decisions: These apply to countries deemed safe by the European Commission, such as Japan, Canada (for commercial organizations), the UK, and the US (under the EU-US Data Privacy Framework) [5].
- Appropriate safeguards: Standard Contractual Clauses or Binding Corporate Rules can be used for countries without adequacy decisions.
- Supplementary measures: Following the Schrems II ruling, exporters must assess whether foreign laws weaken data protection. If so, strong encryption is often required [5].
The European Data Protection Board reinforces the need for diligence:
Data exporters are responsible for verifying, on a case-by-case basis, whether the law or practice of the non-EEA country impinges... on the effectiveness of the appropriate safeguards.
Emerging technologies like homomorphic encryption are gaining attention in 2026. This method enables healthcare organizations to analyze encrypted data without decrypting it, offering a promising solution for compliance with global privacy laws like GDPR, CCPA, and HIPAA. Michal Wachstock of Duality Technologies notes:
Encryption locks down data, allowing healthcare organizations to protect their data, and ensuring compliance with global privacy laws such as GDPR, CCPA, and HIPAA regulations.
PIPEDA, APPI, and HITECH Encryption Standards
Beyond HIPAA and GDPR, other frameworks like HITECH, PIPEDA, and APPI also shape encryption practices for healthcare data. Each takes a unique approach:
- HITECH (USA): This framework extends HIPAA by incentivizing encryption through a "Safe Harbor" provision. Data encrypted using NIST standards (e.g., AES-256) is considered "unusable, unreadable, or indecipherable", exempting organizations from breach notification requirements if lost or stolen. HITECH specifically references NIST SP 800-111 for data at rest and NIST SP 800-52 for data in transit.
- PIPEDA (Canada): Canada’s privacy law employs a principle-based approach, requiring "reasonable" safeguards proportional to the data's sensitivity. For highly sensitive healthcare data, the Privacy Commissioner expects the strongest commercially available encryption. As Canada transitions to the Consumer Privacy Protection Act (CPPA) under Bill C-27, enforcement is becoming stricter, with higher penalties for poor data protection practices.
- APPI (Japan): Japan’s privacy law emphasizes "necessary and appropriate measures" for security. Encryption is a key "Technical Security Control Measure" for both data at rest and in transit, particularly for "Special Care-Required Personal Information" like healthcare data. APPI also enforces strict cross-border data transfer rules, requiring encryption to ensure equivalent protection when data is sent to jurisdictions not recognized by Japan’s Personal Information Protection Commission.
Here’s a quick comparison of these frameworks:
| Feature | HITECH (USA) | PIPEDA/CPPA (Canada) | APPI (Japan) |
|---|---|---|---|
| Primary Driver | Breach Notification Safe Harbor | Principle of "Reasonable Safeguards" | Technical Security Control Measures |
| Specific Algorithm | NIST-aligned (AES-256, RSA) | Technology-neutral (Industry standard) | Technology-neutral (PPC recommended) |
| Legal Structure | Prescriptive (via NIST standards) | Principle-based (Sensitivity-driven) | Guideline-based (PPC oversight) |
Despite their differences, a common thread emerges: adopting AES-256 encryption offers a practical solution for meeting compliance in these regions. For U.S. organizations, FIPS 140-3 validation is key to maintaining Safe Harbor status under HITECH. In Canada, organizations must document why their chosen encryption methods are suitable for the data’s sensitivity. In Japan, encryption is critical for any cross-border transfers involving jurisdictions not recognized by the PPC.
Encryption Methods for International Healthcare Data
Handling international healthcare data transfers calls for precise encryption strategies. By tailoring methods for securing data both in transit and at rest, organizations can establish a robust framework that aligns with global compliance requirements like HIPAA and GDPR. Below, we’ll explore key approaches for safeguarding data during transmission, storage, and encryption key management.
Protecting Data in Transit
When healthcare data moves across networks, it’s vulnerable to unauthorized access. To counter this, Transport Layer Security (TLS) 1.2 or 1.3 is widely recognized as the standard for encrypting data in transit, ensuring secure end-to-end communication. According to 45 CFR § 164.312(e), organizations must "implement technical security measures to guard against unauthorized access to electronic protected health information that is being transmitted over an electronic communications network" [8].
Although HIPAA classifies encryption for data in transit as "addressable", this doesn’t mean it’s optional. Organizations are required to evaluate whether encryption is suitable for their specific environment. If encryption isn’t implemented, alternative measures must be documented. The regulation emphasizes the need to "implement a mechanism to encrypt electronic protected health information whenever deemed appropriate" [8].
To bolster security further, organizations can use integrity controls to ensure data isn’t tampered with during transmission and authentication mechanisms to restrict access to authorized users only.
Protecting Data at Rest
Data stored in systems like databases, file servers, or backups demands a different set of encryption tools. Full Disk Encryption (FDE) is one such method, safeguarding entire storage devices by making data unreadable if the hardware is lost or stolen. For healthcare data, AES-256 encryption is a widely accepted standard for securing data at rest.
For more precise control, database-level encryption can be used to encrypt specific tables or columns containing sensitive information, such as patient diagnoses or treatment details. This method ensures that even if unauthorized access occurs, the encrypted data remains unreadable without the proper key. Similarly, file-level encryption is another effective approach, particularly useful for protecting individual patient records or research files.
However, encryption is only as strong as the management of its keys, making secure key practices essential.
Encryption Key Management Best Practices
Encryption can’t succeed without strong key management throughout the key lifecycle - from creation to eventual destruction. As outlined in NIST SP 800-57, "This Recommendation provides general guidance and best practices for the management of cryptographic keying material, including definitions of the security services that may be provided when using cryptography" [9].
Secret and private keys must be shielded from unauthorized access or modification, while public keys require protection to ensure their authenticity and prevent tampering. For international healthcare data transfers, using secure key transport or key agreement protocols is critical to establishing trusted communication channels.
To minimize risks and ensure smooth recovery, organizations should adopt practices like secure backups, regular audits, and automated key rotation. Maintaining a detailed inventory of all cryptographic keys - complete with their purpose, expiration dates, and the specific data they protect - is equally important. All key management activities should take place within validated cryptographic modules that meet stringent security standards.
Encryption Standards and Protocols Comparison
Selecting the right encryption standard isn’t a one-size-fits-all decision, especially for healthcare organizations managing international data transfers. Each encryption method has its strengths, and understanding how these methods compare is key to meeting compliance requirements for regulations like HIPAA and GDPR. Here's how some of the leading encryption standards measure up when it comes to securing healthcare data.
AES (Advanced Encryption Standard) is widely regarded as the go-to option for encrypting large amounts of data. As a symmetric cipher, it uses the same key for both encryption and decryption, making it incredibly fast and efficient for protecting patient records. AES-256, in particular, is considered resistant to brute-force attacks - even from future quantum computers - due to the immense computational power required to break it. This makes it an excellent choice for securing cloud storage and full-disk volumes that hold sensitive healthcare information.
RSA (Rivest–Shamir–Adleman) operates differently, relying on asymmetric encryption with a pair of public and private keys. It's most commonly used for secure key exchanges and digital signatures rather than encrypting large datasets, as its computational demands make it less efficient for such tasks. To maintain security, RSA keys should be at least 2,048 bits long. However, organizations should also prepare to transition to more efficient alternatives, especially when long-term data security is critical.
ECC (Elliptic Curve Cryptography) provides the same level of security as RSA but with significantly smaller key sizes. For example, a 256-bit ECC key offers equivalent security to a 3,072-bit RSA key. This efficiency makes ECC a great fit for resource-limited environments, such as mobile healthcare apps, wearable devices, and IoT technologies, where conserving battery life and bandwidth is vital. It's no surprise that companies like Apple, Google, and Microsoft are increasingly incorporating ECC into their TLS stacks, signaling a broader move toward more efficient cryptographic solutions.
To make these comparisons clearer, here’s a breakdown of key differences among AES, RSA, and ECC:
| Feature | AES | RSA | ECC |
|---|---|---|---|
| Type | Symmetric | Asymmetric | Asymmetric |
| Key Length | 128, 192, 256 bits | 2,048–4,096 bits | 256–384 bits |
| Performance | Very fast (hardware-accelerated) | Slower (computationally heavy) | Fast (optimized for IoT/mobile) |
| Primary Use | Bulk data, cloud storage, databases | Key exchange, digital signatures | Mobile apps, TLS 1.3, IoT devices |
| Quantum Resistance | High (with AES-256) | Low (vulnerable to Shor's algorithm) | Low (vulnerable to Shor's algorithm) |
| Compliance Role | Data at rest/in transit protection | Identity verification/handshake | Modern secure communication |
Modern encryption protocols often combine these methods for maximum efficiency and security. For instance, hybrid encryption uses RSA or ECC for securely exchanging session keys, while AES handles bulk data encryption. This combination reduces latency and ensures compliance, particularly for mobile and IoT healthcare applications. Together, these standards create a strong foundation for meeting international healthcare compliance needs.
Managing Encryption Compliance Challenges
Managing encryption compliance in healthcare requires careful planning and attention to detail across all stages of data transfer. One major challenge is navigating international transfers, especially under regulations like GDPR. The first step is determining whether a transfer qualifies as "restricted." This involves assessing GDPR applicability, identifying who initiates the transfer, and understanding the recipient's legal independence[1]. Even granting access to an overseas organization for support services can count as an international transfer[1].
When no adequacy decision is in place, the complexity increases. Organizations must adopt safeguards like Standard Contractual Clauses (SCCs), International Data Transfer Agreements (IDTA), or Binding Corporate Rules (BCRs)[1][5]. In some cases, additional measures, such as robust end-to-end encryption, are necessary for transfers outside the EEA[5].
Healthcare data often moves through intricate processing chains involving controllers, processors, and sub-processors. This makes it harder to enforce encryption standards consistently across all external entities[5]. To manage this, organizations need to map contracts and data flows meticulously, identifying every entity that may access sensitive data outside their home country[1]. The European Data Protection Board stresses that data exporters must monitor whether adequacy decisions for their transfers remain valid and are not being revoked or invalidated[5]. Addressing these challenges often requires automated and integrated risk management tools.
Censinet RiskOps™ for Encryption Risk Management
Platforms like Censinet RiskOps™ simplify the complexities of encryption compliance. This advanced tool automates key tasks, such as managing compliance across multiple jurisdictions and conducting third-party risk assessments. It also benchmarks cybersecurity practices, helping healthcare organizations document Transfer Risk Assessments (TRAs) and ensure encryption standards align with regulations like HIPAA and GDPR.
Censinet AI™ accelerates the process by allowing vendors to complete security questionnaires in seconds. The system automatically summarizes evidence, captures integration details, and flags potential fourth-party risks. Its central dashboard provides real-time insights into encryption risks across an organization’s vendor ecosystem. By routing critical findings to the right stakeholders, the platform balances automation with human oversight, enabling faster and more precise compliance management.
Managing Encryption Risks with Third-Party Vendors and Cloud Providers
Handling encryption risks extends beyond internal operations to include third-party vendors and cloud providers. Data Processing Agreements play a key role by specifying required security measures and clearly defining vendor responsibilities as data processors, regardless of their location[5]. For non-EEA cloud providers, Standard Contractual Clauses can address scenarios like controller-to-processor (C2P) and processor-to-processor (P2P) transfers[5].
Transfer Impact Assessments (TIAs) are essential for documenting details about each transfer, including the legal environment in the destination country and any supplementary encryption measures in place[5]. Contracts should also require vendors to challenge unauthorized access requests from their local authorities. For multinational healthcare organizations, Binding Corporate Rules (BCRs) offer a way to establish consistent encryption and data handling policies across borders[5]. As the Information Commissioner’s Office points out, organizations relying on safeguards must complete a transfer risk assessment (TRA)[1].
In cases where derogations apply - such as explicit patient consent or contract performance - it’s important to ensure the "necessity test" is met. This means confirming that the transfer is essential for the specific purpose and is not repeated unnecessarily[5]. Derogations should only be used as a last resort when other safeguards, like SCCs, aren’t feasible.
International Healthcare Encryption Implementation Checklist
Implementing encryption strategies for international healthcare requires a clear and systematic approach. To tackle the complexities of encryption compliance, this checklist offers practical steps for setting up effective international encryption measures that align with the standards mentioned earlier.
Compliance Readiness Checklist
Map all data flows and contracts
Start by identifying every point where personal health information crosses borders. Document the roles of data controllers and processors to ensure clarity about compliance responsibilities in these cross-border transfers.
Use the three-step transfer test
For every transfer, evaluate the following:
- Does the transfer fall under regional data protection laws (e.g., UK GDPR or HIPAA)?
- Is the transfer being made to an organization outside your jurisdiction?
- Is the recipient a separate legal entity?
This process helps determine the necessary safeguards for each transfer [1][5].
Choose the correct transfer mechanism
Support international transfers with one of the following:
- Adequacy decisions (e.g., for Canada, Japan, the UK, or the USA under the Data Privacy Framework)
- Safeguards like Standard Contractual Clauses or Binding Corporate Rules
- Specific derogations
If no adequacy decision applies, use the European Commission's Standard Contractual Clauses or the UK's International Data Transfer Agreement [1][5].
Conduct Transfer Risk Assessments (TRA)
When relying on safeguards instead of adequacy decisions, create a TRA or TIA for each transfer. This should include details about the destination country’s laws, specific circumstances of the transfer, and any additional encryption measures [5].
Data exporters must regularly monitor whether relevant adequacy decisions remain valid and ensure they are not revoked or invalidated.
Assign a dedicated team to track these updates.
Document and apply supplementary measures
In light of the Schrems II ruling, evaluate whether the destination country’s laws weaken your safeguards. If they do, implement supplementary measures like robust end-to-end encryption and document these actions [5]. For transfers based on explicit patient consent or contract performance, apply a necessity test to confirm the transfer is essential and not a recurring practice [5]. Additionally, formalize agreements with processors to specify encryption standards, and maintain a centralized system to document vendor capabilities and risks posed by subcontractors.
Conclusion
Encryption has become a non-negotiable requirement in global healthcare regulations. The 2026 updates to the HIPAA Security Rule remove the "addressable" category, making encryption enforcement mandatory in the United States [11][12]. Similarly, the European Health Data Space Regulation, which came into effect in March 2025, demands active technical compliance rather than just documentation [13]. These changes underscore the urgency for healthcare organizations to strengthen their encryption practices, especially as credential theft remains a leading cause of data breaches [12].
Navigating encryption compliance across frameworks like HIPAA in the U.S., GDPR in the EU, and other emerging global standards is no longer as simple as checking boxes. It requires continuous monitoring of vendor encryption practices, automated risk assessments, and centralized oversight of third-party security measures. This is particularly critical as healthcare data flows through cloud platforms, IoT medical devices, and distributed systems [10][14].
To tackle these challenges, Censinet RiskOps™ offers a streamlined solution. This platform replaces outdated, manual assessments with AI-driven, continuous vendor risk management. By automatically identifying gaps against industry benchmarks like NIST CSF and HPH CPGs, it ensures encryption standards are met consistently across jurisdictions, all while reducing the time and costs associated with compliance [10].
Looking ahead, the rise of quantum computing introduces new risks to current encryption methods. Healthcare organizations need to prepare for post-quantum cryptography while staying compliant with existing standards [10]. Adopting a unified security architecture that integrates encryption into both current and future regulatory requirements is essential. By automating encryption risk management today, organizations can better navigate the increasingly complex global compliance landscape of tomorrow.
FAQs
When do cross-border healthcare data transfers trigger GDPR Chapter V rules?
When healthcare data containing personal information is transferred outside the European Economic Area (EEA), GDPR Chapter V rules come into play. These rules cover any instance where personal data is sent across borders, whether it's through direct transmission or by granting access to another controller or processor.
What’s crucial here is that these rules apply if the controller or processor involved in the transfer is subject to GDPR for that specific processing activity. This ensures that personal data remains protected, even when it moves beyond the EEA's boundaries.
What key management steps are required to keep encrypted ePHI in HIPAA safe harbor?
To ensure encrypted ePHI (electronic protected health information) remains within HIPAA's safe harbor guidelines, it's critical to follow a few key practices:
- Store encryption keys separately: Always keep encryption keys in a secure location, separate from the encrypted data itself. This reduces the risk of unauthorized access.
- Regularly rotate encryption keys: Updating keys on a routine basis helps maintain security and minimizes vulnerabilities.
- Implement role-based access controls: Restrict access to encryption keys and sensitive data based on users' roles, ensuring only authorized personnel can access them.
These measures align with HIPAA's requirements and help protect sensitive healthcare information effectively.
How do you determine if supplementary encryption is necessary after Schrems II?
Evaluating whether additional encryption is necessary after Schrems II requires a careful look at the risks tied to international data transfers and the strength of existing protections. Using strong encryption methods can provide effective protection, but only if the encryption keys are controlled by the data exporter or trusted parties within the European Economic Area (EEA). It's also crucial to examine the legal landscape of the destination country to determine whether encryption alone addresses the risks. If not, you may need to implement extra safeguards.


